Reduce the workload of manual analyses by 90%. The clarity, speed, and reliability of VMRay’s analyses maximizes the performance of DFIR and CERT teams.
What is Incident Response?
Incident response is a comprehensive cybersecurity strategy that involves detecting, containing, and mitigating security threats. It combines reactive measures to address current breaches with proactive tactics like threat hunting to prevent future incidents, ultimately strengthening an organization’s overall security posture.
Global Top 10 Technology Company | Threat Intelligence Team
For traditional security stack deployments, zero-day malware, Advanced Persistent Threats (APTs), and targeted phishing attacks can be especially difficult to detect and analyze.
Third party validation is critical to ensuring that suspicious threats are not dismissed as false positives and released back into the enterprise.



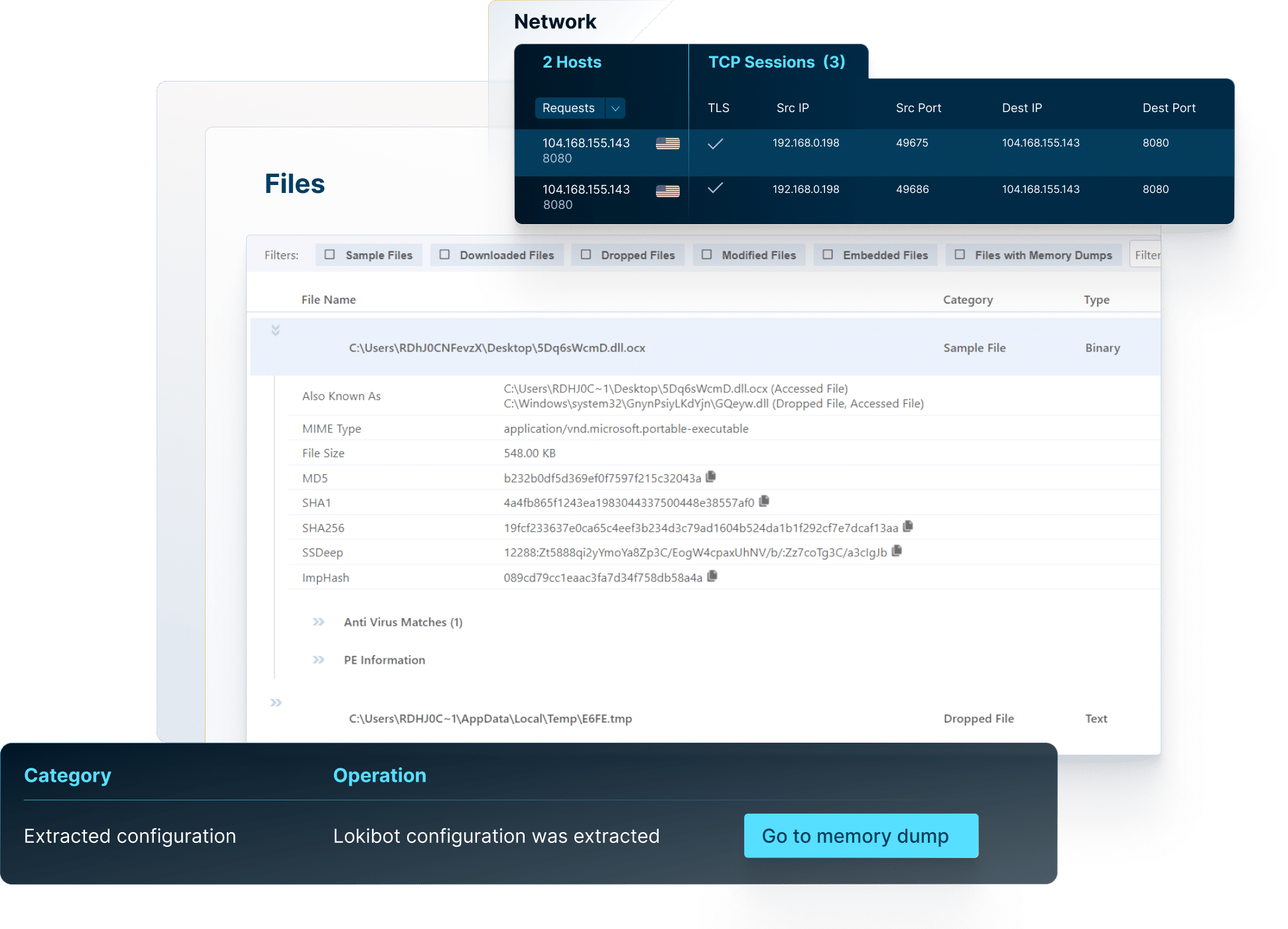
VMRay can observe, log and report malicious activities all the way to the end of their execution. This way, the VMRay incident response platform provides an in-depth picture of the malware and phishing samples.
With its hypervisor-based sandboxing technology, VMRay remains invisible to even the most evasive malware. This enables comprehensive threat analysis with accurate results.
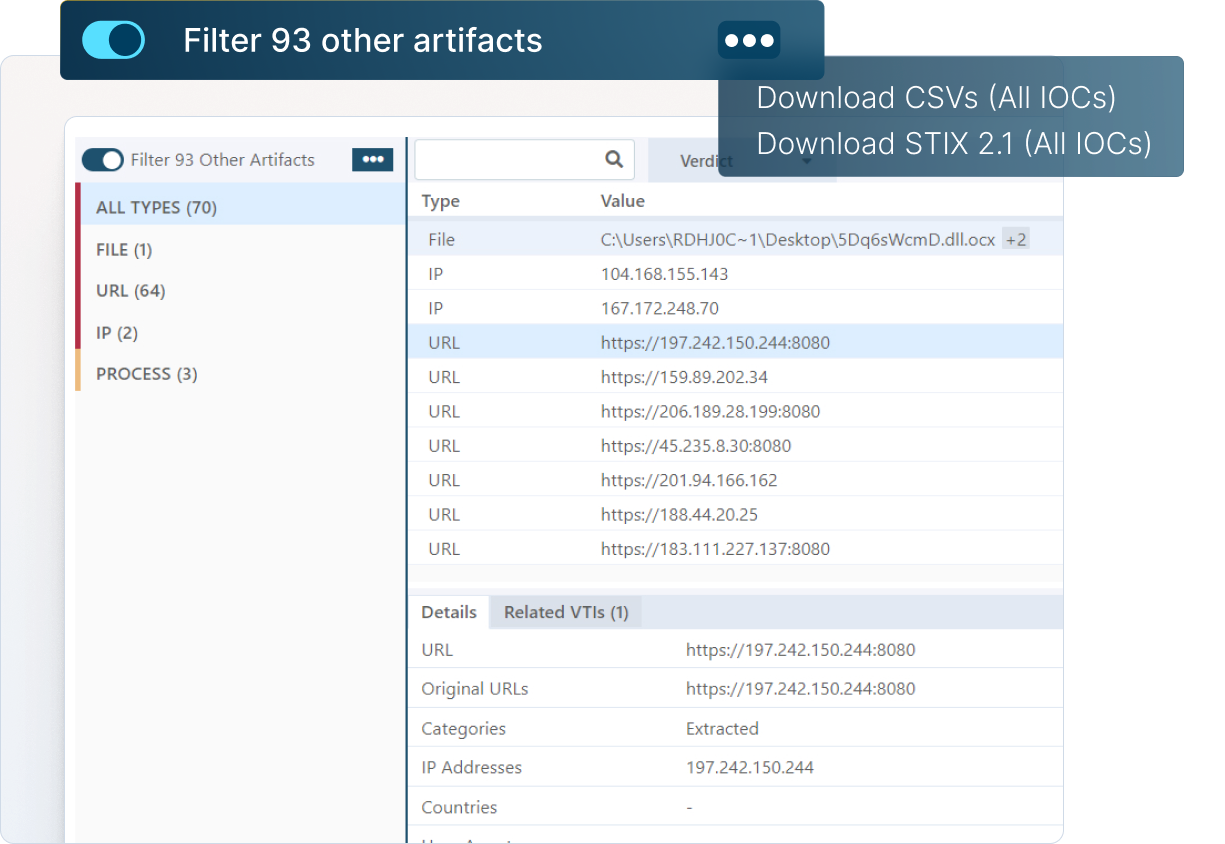
Your organization can extract threat intelligence with VMRay’s clear reports and pre-filtered IOCs. Unlike the third-party threat repositories, this intel is highly relevant to the threats your organization is facing.
Definitive verdicts support accurate, automated incident management
EDR and XDR solutions when combined with a SIEM or SOAR solution can correlate data across a broader spectrum of disparate security devices, including endpoint, network activity. With VMRay, definitive malware verdicts support assured, automated response actions.



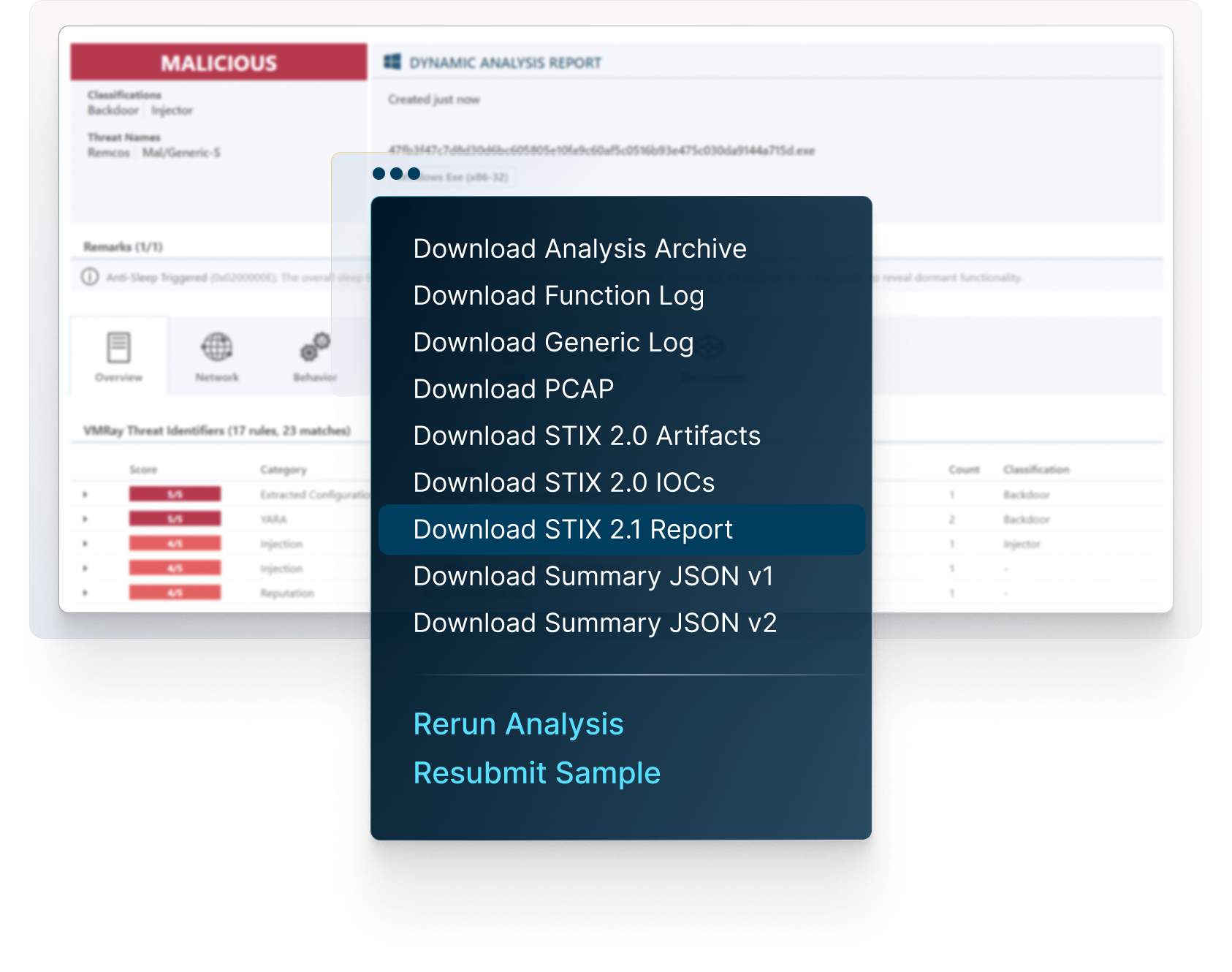
Check the full reports, explore the network connections, see the details on malicious behavior, map the threat on MITRE ATT&CK Framework, download IOCs and artifacts, and much more.
The VMRay platform performs automated malware triage and phishing analysis of samples submitted either manually or via API integration into many of the leading Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Security Orchestration, Automation and Response (SOAR) and Threat Intelligence Platforms (TIP) security solutions.
While the VMRay platform does not directly perform automated incident response actions, the definitive verdict of malicious or benign malware submissions enables EDR/XDR/SOAR solutions to make confident, automated response actions via playbooks and workflows to critical incidents.
For incident response automation to be successful, suspicious or previously unknown malware or phishing alerts from EDR/XDR/SOAR solutions must be fully analyzed using Dynamic Analysis to identify any malicious behavior and the extraction of IOCs. The IOCs can then be used in the incident response process to fully mitigate the threat.
The sophistication of phishing emails today allows a small number to bypass perimeter email gateways and point phishing solutions, increasing the risk of human error to occur. End users not educated in identifying malicious phishing emails may accidently click on a malicious attachment or link by mistake, putting their organization at risk of a breach.
VMRay’s User Reported Phishing feature, combined with end-user education on phishing threats allows organizations to supplement their detection fabric with human eyeballs trained to spot potentially malicious email threats. These phishing threats can then be forwarded to the VMRay abuse mailbox and automatically analyzed without SOC intervention. If the email is malicious, the end user is notified, and the SOC receives the final analysis and IOCs used to mitigate the threat, speeding incident resolution.
VMRay integrates via API with the following EDR, XDR, SIEM, SOAR and TIP solutions.
EDR/XDR Integrations
SentinelOne, Microsoft Defender for Endpoint, and CrowdStrike
SIEM Integrations
Splunk SIEM, IBM QRadar
SOAR Integrations
Google Chronicle SOAR, Palo Alto Networks Cortex XSOAR, Splunk SOAR
TIP Integrations
Anomali, Cyware, MISP, ThreatConnect, ThreatQ
VMRay’s value proposition goes beyond exceptional products, focusing on high-quality professional services and 24/7 customer support that eliminate skills gaps and drive success in dynamic cybersecurity environments to accelerate incident resolution.
Recognizing resource constraints faced by Security/IT teams, VMRay offers a comprehensive suite of services tailored for seamless onboarding, optimized configuration, and robust integrations – ensuring efficient deployment and maximizing solution efficacy.
VMRay addresses deployment concerns by offering a range of professional service offerings to get you up and running quickly. We leverage our expertise deploying hundreds of customers to ensure that you are up and running regardless of how complex your requirements may be.
X-press Onboarding
Our express onboarding service ensures a swift deployment while our expert team assists with configuration and provides guidance. Whether you’ve selected to utilize the VMRay Cloud or and on-premises solution, we will work with you to get the VMRay platform set up and configured to your requirements.
Automation Integration Deployment
Seamlessly integrate our solutions with your existing tools to enhance incident automation and strengthen your cybersecurity infrastructure. If your needs include taking advantage of the time and labor savings of integrating VMRay into your security ecosystem, we will work with you to configure our range of connectors to 3rd party platforms to other solutions within your environment.
Bespoke Training
Empower your team with tailored training options, including video recordings, accessible PDF materials, and in-person sessions. Basic training is provided during the on-boarding process and a variety of free training resources, both documentation and videos. Sometime customers want a more customized training solution to better align with their incident response plans. We will work with you to understand your specific requirements and deliver customized instructor based live training tailored to your specific needs.
The VMRay cloud-based platform receives reputational and static engine updates as they become available and are automatically uploaded to the cloud by VMRay.
The Dynamic Analysis uses thirty different types of technology including thousands of YARA Rules to identify malicious behavior. New YARA rules are created and added frequently between each major quarterly release to ensure the platform reflects the current and evolving threat landscape.
🚀 Meet UniqueSignal: the actionable malware intelligence VMRay powers. 60 Days FREE TRIAL - Available For A LIMITED TIME.