
Phishing continues to drain valuable time from Security Operations Centers, with manual email investigations slowing down response and overloading teams. In this on-demand webinar, you’ll discover how VMRay’s automated detonation and deep threat analysis can dramatically speed up phishing triage, reduce manual effort, and improve accuracy. Learn practical ways to

Catch the latest insights and stay ahead of evolving cyber threats with the latest insights from our April Detection Webinar! Join Tony Lambert from Red Canary alongside Patrick Staubmann and Ertugrul Kara from VMRay as they unveil new detection techniques, including a VTI for CPU property queries, advanced YARA rules

Watch the March 2025 edition of our “Threat Detection Highlights” webinar series to explore the latest advancements in malware detection and EDR integration. In this session, our experts highlight new YARA rules targeting threats like SparkRAT, StrelaStealer, and SocGholish, and unveil a new VTI for detecting Interactive Process Hollowing. You’ll

SOC and CERT teams constantly battle evasive malware, overwhelming alert volumes, and time-consuming manual investigations. VMRay’s best-of-breed malware sandbox is built to help security teams streamline analysis, validate threats faster, and enhance automation—without the blind spots of traditional solutions. In this technical deep dive, the VMRay Team will showcase how

Watch the February 2025 edition of our “Threat Detection Highlights” webinar series to stay ahead of evolving cyber threats. In this session, our experts will walk you through key updates and practical strategies to address the most pressing cyber threats, including Pastejacking, BruteRatel C2, and Residential VPN evasion tactics. You’ll

In today’s evolving cyber threat landscape, adversaries are constantly refining their tactics to evade detection, making it imperative for SOC teams, CTI analysts, and security leaders to elevate their threat intelligence (CTI) capabilities beyond static indicators. The key to proactive defense lies in behavioral malware analysis, which uncovers deep adversary

Watch the January 2025 edition of our “Threat Detection Highlights” webinar series to stay ahead of evolving cyber threats. This session covers fresh threat intelligence on the latest phishing kits, phishkit.srj and phishkit.blur, and techniques to detect them before they strike. Explore the breakdown of the Concatenated ZIP evasion tactic

Discover how advanced malware analysis empowers government cybersecurity teams to outmaneuver adversaries. In this exclusive webinar, VMRay experts dive into the latest threat modeling strategies, demonstrating how intelligence-driven insights can transform your cybersecurity operations. Explore the power of the Diamond Model of Intrusion Analysis, adversary playbooks, and real-world case studies

Watch the end of year edition of our ‘Threat Detection Highlights’ webinar. With 2025 on the horizon, attackers continue to refine their evasion techniques. VMRay Labs team has been tirelessly researching trends and shipping updates to counter these threats. Our product team showcases these latest updates, engineered to add muscle
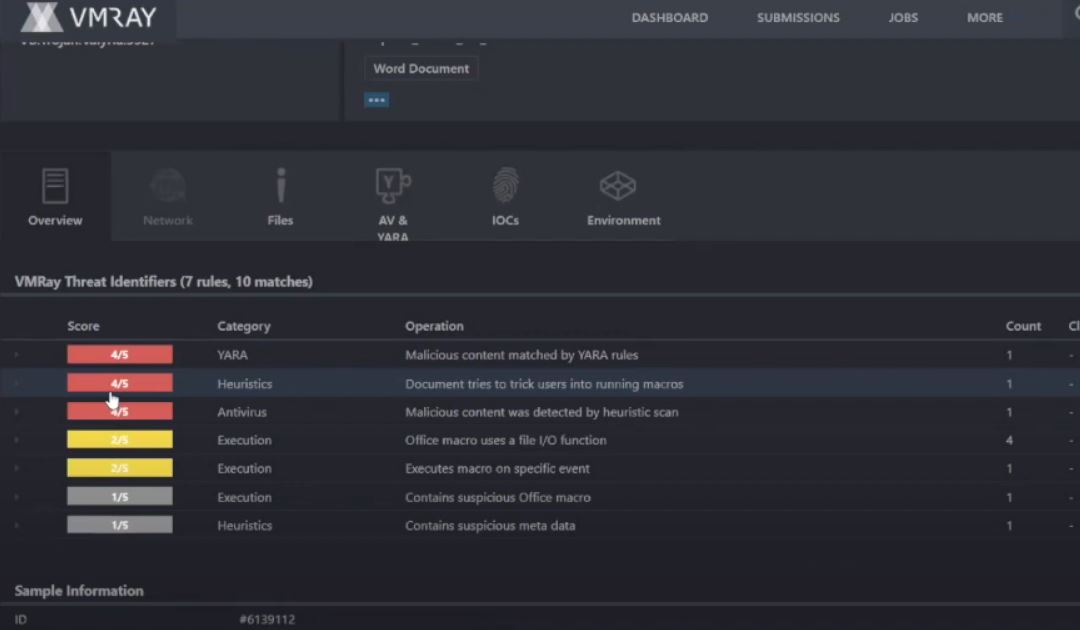
Catch the on-demand webinar featuring VMRay’s Sr. Product Manager Andrey Voitenko and Technical Field Ops Lead Michael Bourton, where they share insights on evaluating and optimizing your sandbox to combat advanced malware. Learn how to stress-test your sandbox with tools like Pafish and al-khaser, identify evasion techniques used by threats,
Keep up to date with our weekly digest of articles. Get the latest news, invites to events, and threat alerts!
🚀 Meet UniqueSignal: empower your security operations with precise and actionable threat intelligence!