Get proactive by analyzing threats in the wild.
Elevate your Detection Engineering with the most accurate analysis artifacts.

Global Top 10 Technology Company | Threat Intelligence Team
Detection engineers face millions of new malware types daily. Each type needs special skills for careful and accurate analysis. The lengthy research for prioritizing alerts further hinders the practical aspects of threat detection engineering.
Although threat intelligence is vital, detection engineers frequently lack essential contextual information. The absence of insights from Digital Forensics and Incident Response (DFIR) and Cyber Threat Intelligence (CTI) teams complicates the threat-hunting process. To keep up, engineers must constantly revise their strategies. This highlights the need for advanced methods in threat detection and intelligence gathering.





Discover the most unique and intriguing strings, process names and command lines to generate scalable detection rules with YARA, SIGMA or SNORT.
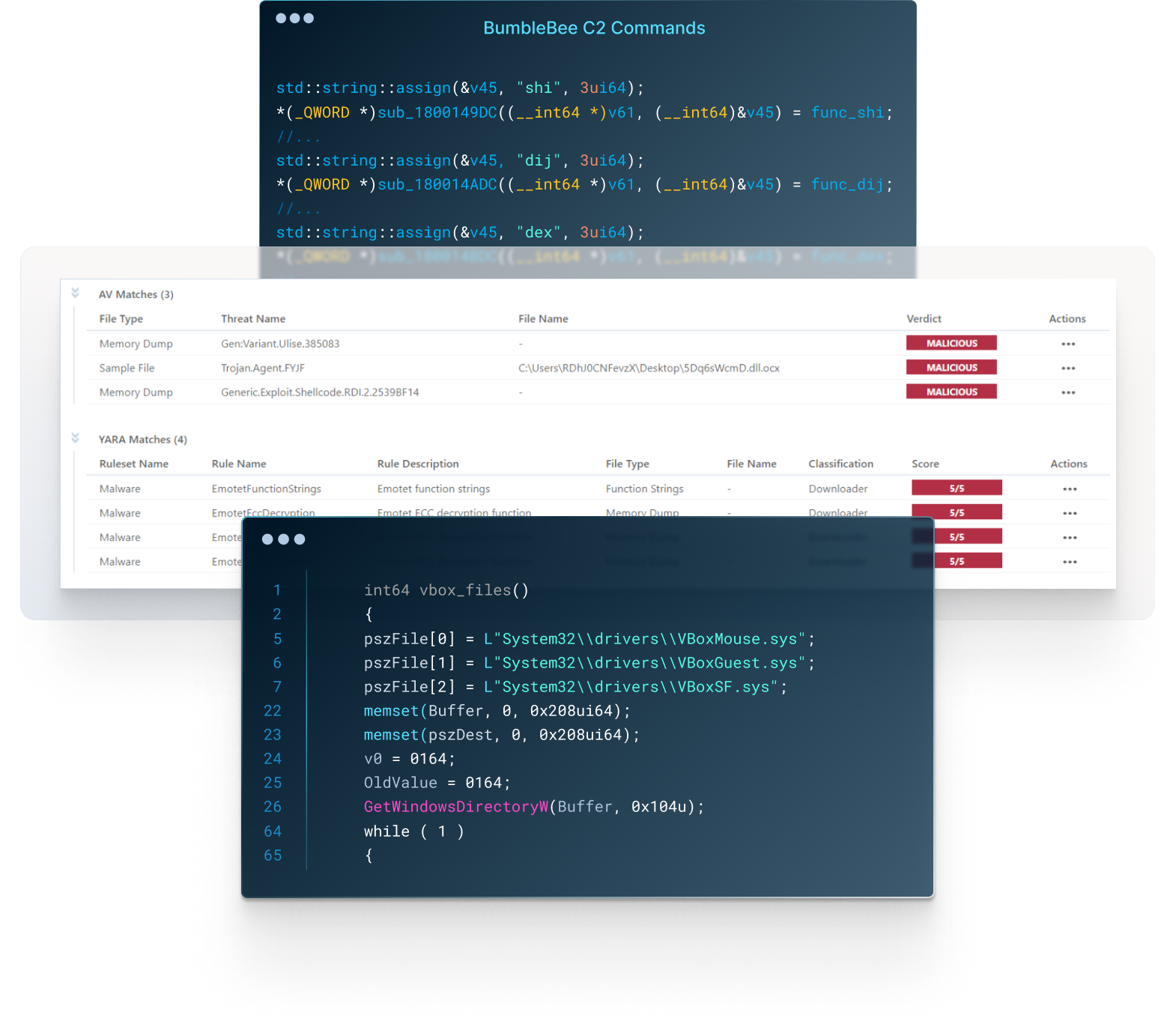
The built-in malware configuration extractors of VMRay can do the necessary de-obfuscation and family-specific data parsing.
Build solid detections through correct classification which will allow you to move up on the pyramid of pain from only IOCs to TTPs.
VMRay’s robust detection coverage will alert your security team to embedded content, including function call strings, from the most prolific malware samples, no matter how deep they were hidden.
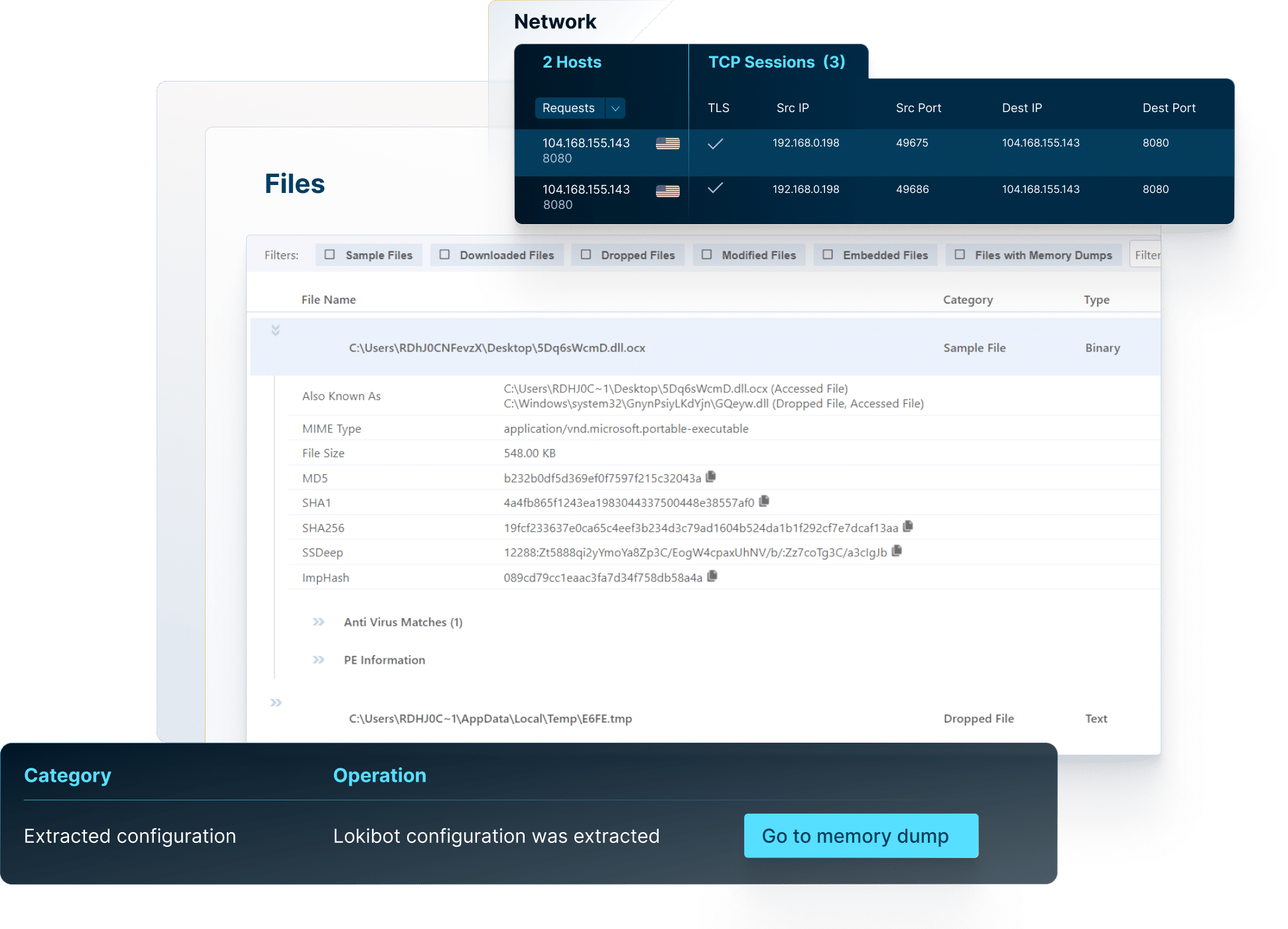
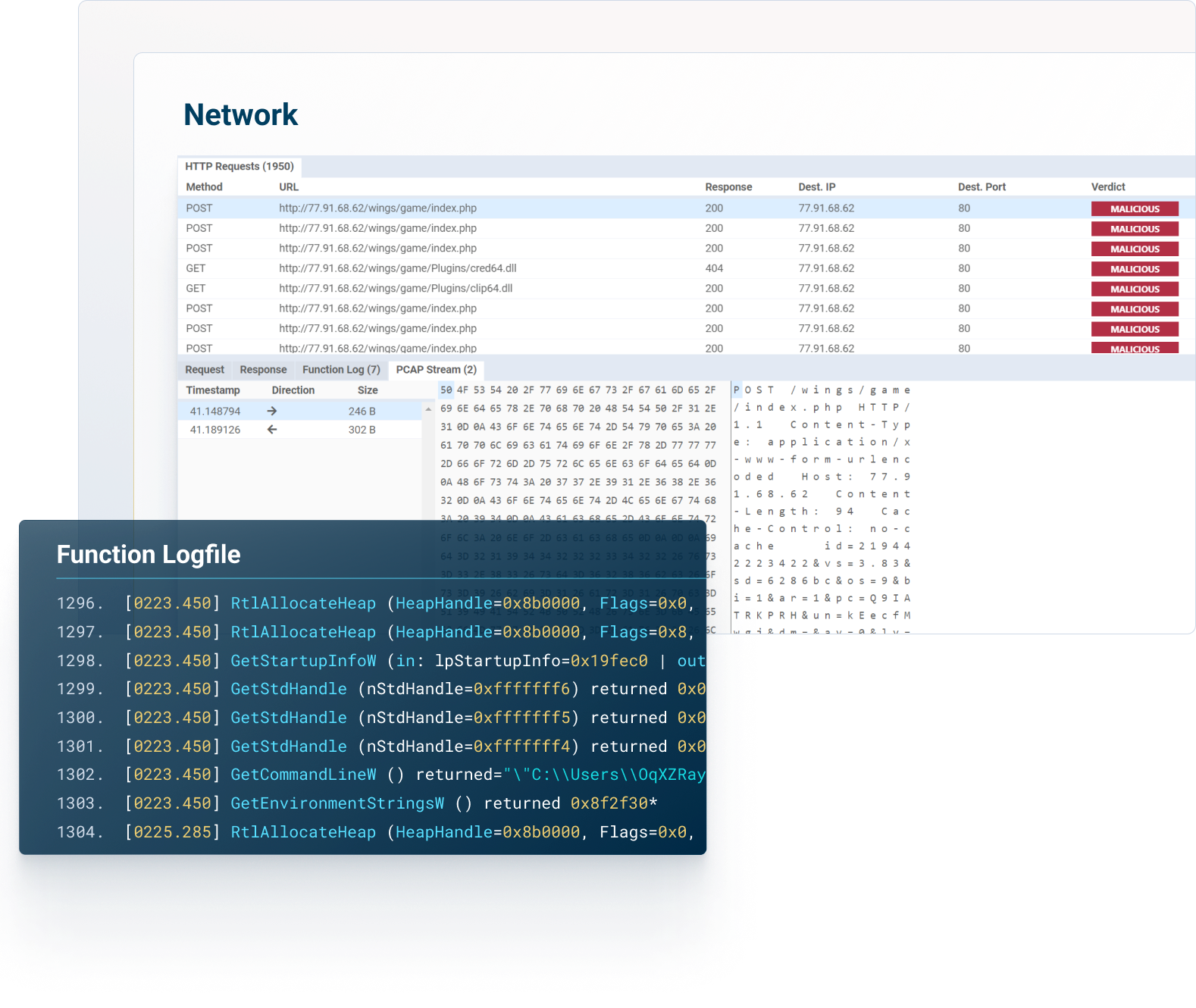
VMRay supercharges your threat hunting and detection by simplifying complex threat data so it’s easier to act and improve your security operations with minimal effort.
The platform allows you to safely analyze suspicious files and URLs by creating a secure environment where you can observe their behavior without risking your systems.
With its easy-to-use interface, VMRay lets you easily navigate data. This way, you can focus on what really matters: protecting your organization.




Access comprehensive reports, explore network connections, get insight into malicious behaviors, map threats to the MITRE ATT&CK Framework, download IOCs and artifacts, and much more.
Over the last few years, Detection Engineering has evolved to a dedicated role to develop and maintain firewall rules, email policy rules, and IDS/IPS detection signatures that can accurately identify and block current and future threats. Detection engineers ensure systems are scalable, reliable, and efficient, while optimizing them to reduce false positives and negatives.
Detection engineers use their knowledge and expertise in network architectures, operating systems, and programming languages to create rules and signatures to recognize and mitigate potential threats. The faster a threat is detected, the less impact it will have on the system or network, mitigating potential damages.
Threat feeds can be incorporated into the workflow to provide IOCs for generic threats, while sandbox technology such as VMRay can extract IOCs from custom-crafted malicious files and URLs specifically targeting an organization. These IOCs are then used to create the rules and signatures needed to mitigate or block these targeted attacks.
VMRay’s sandbox technology uses three different types of analysis. Reputational, static, and dynamic analysis.
Reputational analysis provides a database of known malicious file hashes. If the file hash matches one of the entries in the database, the file is flagged malicious.
Static signatures detect known malware once it has been identified and a signature created. While using static signatures alone will not detect advanced, unknown malware, they are still an integral layer in the overall protection architecture.
Dynamic analysis provides an additional depth of insight by which the malicious file or URL is “detonated” in a sandbox environment and monitored to identify potentially malicious behavior. The monitored results are then handed off to multiple analysis technologies to create a report and supply a verdict of malicious or benign.
Yes. VMRay integrates via API with the following EDR, XDR, SIEM, SOAR and TIP solutions.
EDR/XDR Integrations
SentinelOne, Microsoft Defender for Endpoint, and CrowdStrike
SIEM Integrations
Splunk SIEM, IBM QRadar
SOAR Integrations
Google Chronicle SOAR, Palo Alto Networks Cortex XSOAR, Splunk SOAR
TIP Integrations
Anomali, Cyware, MISP, ThreatConnect, ThreatQ
The integration typically takes minutes, not hours or days and the Detection Engineering team can fully automate their processes for extracting malware threat intelligence and automating responses.
VMRay’s value proposition goes beyond exceptional products, focusing on high-quality professional services and 24/7 customer support that eliminate skills gaps and drive success in dynamic cybersecurity environments to accelerate incident resolution.
Recognizing resource constraints faced by Security/IT teams, VMRay offers a comprehensive suite of services tailored for seamless onboarding, optimized configuration, and robust integrations – ensuring efficient deployment and maximizing solution efficacy.
VMRay addresses deployment concerns by offering a range of professional service offerings to get you up and running quickly. We leverage our expertise deploying hundreds of customers to ensure that you are up and running regardless of how complex your requirements may be.
X-press Onboarding
Our express onboarding service ensures a swift deployment while our expert team assists with configuration and provides guidance. Whether you’ve selected to utilize the VMRay Cloud or and on-premises solution, we will work with you to get the VMRay platform set up and configured to your requirements.
Automation Integration Deployment
Seamlessly integrate our solutions with your existing tools to enhance incident automation and strengthen your cybersecurity infrastructure. If your needs include taking advantage of the time and labor savings of integrating VMRay into your security ecosystem, we will work with you to configure our range of connectors to 3rd party platforms to other solutions within your environment.
Bespoke Training
Empower your team with tailored training options, including video recordings, accessible PDF materials, and in-person sessions. Basic training is provided during the on-boarding process and a variety of free training resources, both documentation and videos. Sometime customers want a more customized training solution to better align with their incident response plans. We will work with you to understand your specific requirements and deliver customized instructor based live training tailored to your specific needs.
Yes. VMRay provides integrations into many of the leading EDR/XDR/SIEM/SOAR and TIP solutions to automate malware triage and analysis. By seamlessly integrating into workflows and playbooks, the entire process of threat identification and mitigation can be fully automated.




Ready to stress-test your malware sandbox? Join us for a no-fluff, all-demo webinar that shows you real techniques to evaluate and optimize your sandboxing solution!